Getty Images
Academic researchers have discovered serious vulnerabilities in the core of Threema, an instant messenger that its Switzerland-based developer says provides a level of security and privacy “no other chat service” can offer. Despite the unusually strong claims and two independent security audits Threema has received, the researchers said the flaws completely undermine assurances of confidentiality and authentication that are the cornerstone of any program sold as providing end-to-end encryption, typically abbreviated as E2EE.
Threema has more than 10 million users, which include the Swiss government, the Swiss army, German Chancellor Olaf Scholz, and other politicians in that country. Threema developers advertise it as a more secure alternative to Meta’s WhatsApp messenger. It’s among the top Android apps for a fee-based category in Switzerland, Germany, Austria, Canada, and Australia. The app uses a custom-designed encryption protocol in contravention of established cryptographic norms.
The seven deadly flaws
Researchers from the Zurich-based ETH research university reported on Monday that they found seven vulnerabilities in Threema that seriously call into question the true level of security the app has offered over the years. Two of the vulnerabilities require no special access to a Threema server or app to cryptographically impersonate a user. Three vulnerabilities require an attacker to gain access to a Threema server. The remaining two can be exploited when an attacker gains access to an unlocked phone, such as at a border crossing.
Paterson et al.
“In totality, our attacks seriously undermine Threema’s security claims,” the researchers wrote. “All the attacks can be mitigated, but in some cases, a major redesign is needed.”
The seven vulnerabilities the researchers uncovered include:
- External actor with no special access
- In the event an ephemeral key is exposed even once, an attacker can permanently impersonate the client to the server and then obtain all metadata in all E2EE messages. This is a remarkable shortcoming because ephemeral keys should never be able to authenticate a user. With Threema, leaking of an ephemeral key has the same effect as leaking a long-term key. Sloppy key management also causes Threema to reuse ephemeral keys in places they should never be reused.
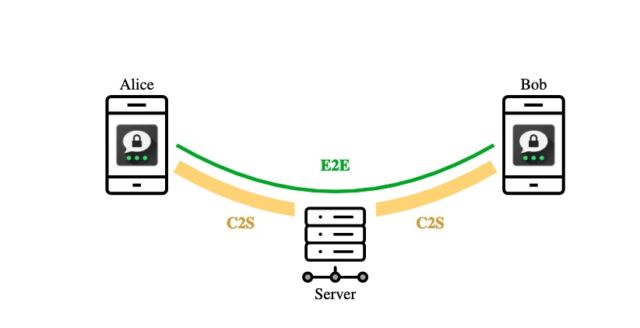
- A flaw in the way Threema’s client-to-server (C2S) protocol interacts with its end-to-end (E2E) protocol that causes a user to create a special Threema value known as a vouch box and send it to the attacker. The attacker can exploit it by tricking a user into sending a set of characters (u9j6ߓ’jjखԻ^߃1כW:-́;ܡRA) to a special but innocuous account. One possible way for an attacker to do this is to send spam to a large number of users that tells them to send the character string to a specific account in order to be eligible for a prize. From that point on, the attacker can impersonate the hacked client to the server.
 Enlarge / Attack 1.2 in practice: on the left, a suitable keypair that is base64 encoded. The public key bytes 1 to 31 , also encoded in the QR code, all consist of printable UTF-8 characters. On the right, the *LYTAAAS Threema gateway account (since revoked), with the hijacked public key of the server. User U sending the contents of the QR to *LYTAAAS as a message will allow *LYTAAAS to authenticate to Threema as the U.
Enlarge / Attack 1.2 in practice: on the left, a suitable keypair that is base64 encoded. The public key bytes 1 to 31 , also encoded in the QR code, all consist of printable UTF-8 characters. On the right, the *LYTAAAS Threema gateway account (since revoked), with the hijacked public key of the server. User U sending the contents of the QR to *LYTAAAS as a message will allow *LYTAAAS to authenticate to Threema as the U.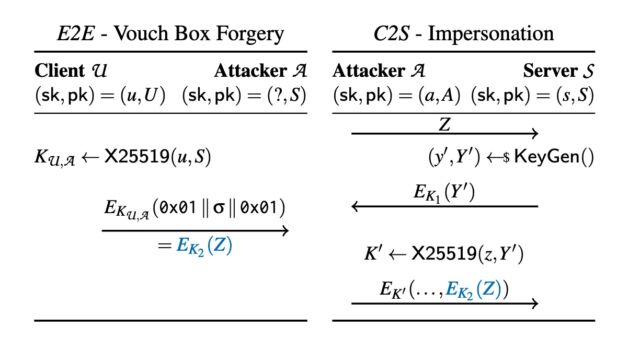 Enlarge / A figure showing the cross-protocol interaction of an E2E and a C2S session. The attacker claims the public key of the server and knows a keypair of the form (z, Z = 0x01 ∥ σ ∥ 0x01). They convince the victim U to send σ to them as an E2E text message (in blue, Left side). The attacker can now start a session of the C2S protocol (Right side) where they use the “ephemeral” keypair (z, Z) and the corresponding vouch box EK2 (Z) (in blue) in order to authenticate as U to the server.
Enlarge / A figure showing the cross-protocol interaction of an E2E and a C2S session. The attacker claims the public key of the server and knows a keypair of the form (z, Z = 0x01 ∥ σ ∥ 0x01). They convince the victim U to send σ to them as an E2E text message (in blue, Left side). The attacker can now start a session of the C2S protocol (Right side) where they use the “ephemeral” keypair (z, Z) and the corresponding vouch box EK2 (Z) (in blue) in order to authenticate as U to the server.
- When an attacker has compromised a Threema server:
- A lack of integrity protection on the message metadata. As a result, an attacker can surreptitiously reorder and/or delete messages sent from one client to another.
- Faulty usage nonce handling allows for “replay and reflection” attacks, in which the threat actor resends old messages and sends a user a message that user previously sent to someone else.
- A bug in the challenge-and-response protocol used for a client to authenticate itself to the server during registration. During the process, the client proves possession of its private key by encrypting a server-chosen message that’s encrypted with a server-chosen public key. A compromised server can exploit this design to create “kompromat,” or potentially incriminating messages that can be delivered at any later time to a targeted user. Threema patched this vulnerability in December 2021, when a separate researcher spotted it.
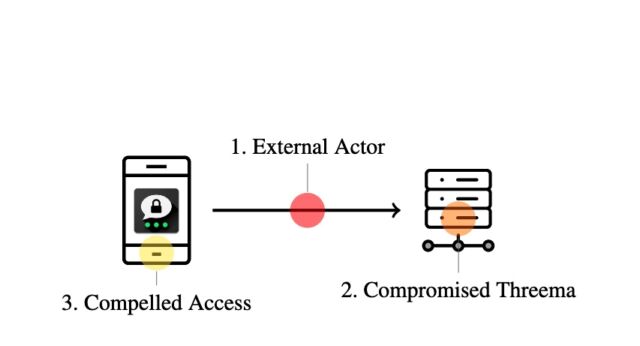
- When an attacker gains access to an unlocked phone running Threema:
- A feature that allows users to export their private key from one device to another. Poor design decisions make it trivial for an attacker to use the key to clone a Threema account and go on to access all future messages. Combined with a compromised Threema server, the adversary can also obtain all previously sent messages.
- Message compression that occurs before encryption when Threema creates a backup, combined with the ability for an attacker to use a nickname feature to inject chosen strings into the backup. This allows a more sophisticated attacker to observe the size of the backup file over multiple iterations and eventually recover the user’s private key.