Linux has yet another high-severity vulnerability that makes it easy for untrusted users to execute code capable of carrying out a host of malicious actions including installing backdoors, creating unauthorized user accounts, and modifying scripts or binaries used by privileged services or apps.
Dirty Pipe, as the vulnerability has been named, is among the most serious Linux threats to be disclosed since 2016, the year another high-severity and easy-to-exploit Linux flaw (named Dirty Cow) came to light as it was being used to hack a researcher’s server. Researchers in 2016 demonstrated how to exploit Dirty Cow to root any Android phone regardless of the the mobile OS version. Eleven months later, researchers unearthed 1,200 Android apps in third-party markets that maliciously exploited the flaw to do just that.
When Nobody becomes all powerful
The name Dirty Pipe is meant to both signal similarities to Dirty Cow and provide clues about the new vulnerability’s origins. “Pipe” refers to a pipeline, a Linux mechanism for one OS process to send data to another process. In essence, a pipeline is two or more processes that are chained together so that the output text of one process (stdout) is passed directly as input (stdin) to the next one.
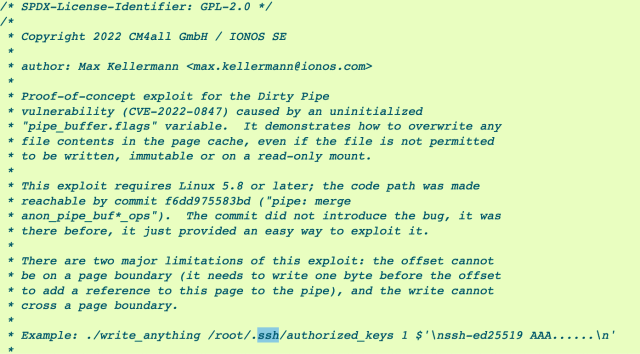
Tracked as CVE-2022-0847, the vulnerability came to light when a researcher for website builder CM4all was troubleshooting a series of corrupted files that kept appearing on a customer’s Linux machine. After months of analysis, the researcher finally found that the customer’s corrupted files were the result of a bug in the Linux kernel.
The researcher—Max Kellermann of CM4all parent company Ionos—eventually figured out how to weaponize the vulnerability to allow anyone with an account—including least privileged “nobody” accounts—to add an SSH key to the root user’s account. With that, the untrusted user could remotely access the server with an SSH window that has full root privileges.
Other researchers quickly showed that the unauthorized creation of an SSH key was only one of many malicious actions an attacker can take when exploiting the vulnerability. This program, for instance, hijacks an SUID binary to create a root shell, while this one allows untrusted users to overwrite data in read-only files:
Other malicious actions enabled by Dirty Pipe include creating a cron job that runs as a backdoor, adding a new user account to /etc/passwd + /etc/shadow (giving the new account root privileges), or modifying a script or binary used by a privileged service.
“It’s about as severe as it gets for a local kernel vulnerability,” Brad Spengler, president of Open Source Security, wrote in an email. “Just like Dirty Cow, there’s essentially no way to mitigate it, and it involves core Linux kernel functionality.”
The vulnerability first appeared in Linux kernel version 5.8, which was released in August 2020. The vulnerability persisted until last month, when it was fixed with the release of versions 5.16.11, 5.15.25 and 5.10.102. Virtually all distributions of Linux are affected.
Throwing a wrench in Android
Dirty Pipe also afflicts any release of Android that’s based on one of the vulnerable Linux kernel versions. Since Android is so fragmented, affected device models can’t be tracked in a uniform basis. The latest version of Android for the Pixel 6 and the Samsung Galaxy S22, for instance, run 5.10.43, meaning they’re vulnerable. A Pixel 4 on Android 12, meanwhile, runs 4.14, which is unaffected. Android users can check which kernel version their device uses by going to Settings > About phone > Android version.
“The Dirty Pipe vulnerability is extremely serious in that it allows an attacker to overwrite—temporarily or permanently—files on the system they should not be able to change,” Christoph Hebeisen, head of security research at mobile security provider Lookout, wrote in an email. “Attackers can use this to change the behavior of privileged processes, effectively gaining the capability to execute arbitrary code with extensive system privileges.”
The Lookout researcher said the vulnerability can be exploited on Android handsets through a malicious app that elevates its privileges, which by default are supposed to be limited. Another avenue of attack, he said, is to use a different exploit to gain limited code execution (for example, with the system rights of a legitimate app that’s hacked) and combine it with Dirty Pipe so the code gains unfettered root.
While Kellermann said that Google merged his bug fix with the Android kernel in February, there are no indications Android versions based on a vulnerable release of the Linux kernel are fixed. Users should assume that any device running a version of Android based on a vulnerable version of the Linux kernel is susceptible to Dirty Pipe. Google representatives didn’t respond to an email seeking comment.